Network Penetration Testing
DefenceRabbit’s comprehensive network penetration testing fortifies your network infrastructure against sophisticated cyber threats, leveraging decades of proven cybersecurity expertise. Our seasoned security professionals identify a full spectrum of vulnerabilities including deeply hidden and commonly overlooked exposures that automated tools or less experienced testers may miss. With our comprehensive and targeted penetration testing services, your organization can confidently secure its network against evolving attack vectors.
Expose Network Vulnerabilities with Expert Penetration Testing Services
DefenceRabbit’s expert penetration testing services help secure your organization’s networks from cybersecurity vulnerabilities across all potential attack vectors. We specialize in external infrastructure testing, internal network assessments, web application security, and mobile application testing. By identifying security vulnerabilities early, we help prevent breaches, protect sensitive data, and minimize financial risk. Our detailed assessments provide critical insights to strengthen your network security posture, safeguard business continuity, and uphold data integrity against modern cyber threats.
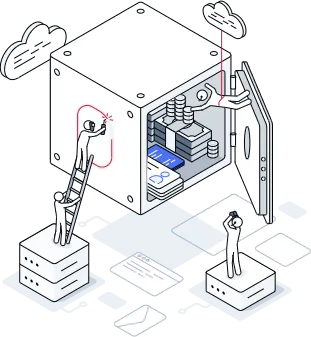
Types of Network Penetration Testing
Network Penetration Testing, also called Infrastructure Penetration Testing, includes Internal and External testing to assess your network security posture comprehensively using top penetration testing tools.
Internal Penetration Testing
An internal penetration test evaluates what a potential attacker could accomplish after gaining initial access to your internal network and identifies insider threats. This simulation helps uncover risks posed by insider threats, including malicious employees, compromised internal devices, or unintentional security lapses.
External Penetration Testing
An External Network Penetration Test targets perimeter security, identifying vulnerabilities in public-facing assets like web servers and DNS using best network penetration testing tools.
Network Penetration
Testing Process
Step 1
Scoping and Planning
We begin with a comprehensive assessment of your organization's network security infrastructure, including system architecture, critical assets, and connected applications. Based on your business needs, we define clear testing objectives, determine the scope of the penetration test, and tailor our strategy to align with your security goals and regulatory compliance requirements.
New Attack Surfaces Require a New Approach to Testing
As cyber threats evolve, DefenceRabbit’s network penetration testing process uses advanced tools and techniques to identify vulnerabilities and strengthen your network security posture.

Why Choose DefenceRabbit
At DefenceRabbit, we specialize in application penetration testing and web application security. Our transparent, collaborative approach uncovers real vulnerabilities, helping you secure your apps and comply with industry standards.
Dedicated to Cybersecurity Excellence
We bring years of hands-on experience and a relentless focus on quality to every engagement, ensuring thorough and reliable security testing.
Safeguard Your Digital Assets
Our experts go beyond automated scans to uncover real threats helping you stay ahead of attackers and defend what matters most.
Data Privacy & Compliance
We help you meet stringent data protection regulations and industry standards, reducing your risk exposure and ensuring regulatory compliance.
Recognized Expertise
Our expert penetration testers bring decades of experience and unmatched technical skill in application security assessments.
Proven Methodology
Whether you opt for a framework-based or goal-oriented strategy, we identify critical risks that automated tools and bug bounty programs often overlook.
Innovative Enablement Platform
Our cutting-edge cybersecurity platform enhances every engagement to boost collaboration and enable our expert engineers to identify critical, high-impact vulnerabilities.
Identify Supply Chain Risk from Third Party AI Products
Enhanced Security Posture
Strengthen your defenses against the latest advancements in AI, ensuring your organization remains resilient in the face of relentless attacks
Address Material Risks
Identify vulnerabilities and weaknesses within your AI systems, while tailoring solutions to address and mitigate the risks
Build Trust Through Compliance
Demonstrate compliance with industry standards such as NIST AI RMF and build trust among clients and partners
Ready to Discuss Your Network Penetration Testing Initiative?
DefenceRabbit's offensive security experts specialize in red teaming pen testing and simulated cyber attacks, ready to answer your questions and help improve your security posture.
FAQ